How to Find and Claim Profitable Crypto Airdrops
Learn how to find, verify, and claim profitable crypto airdrops safely. This GrindToCash guide reveals trusted tools, early alerts, and real strategies.
By Yaser | Published on October 31, 2025
What Crypto Airdrops Are—and Why They Exist
Airdrops distribute tokens to users to kick-start network effects, reward early participation, and decentralize ownership. Teams use them to seed real communities, gather feedback, and align incentives without expensive advertising. In practice, you “earn” by qualifying—not by buying—so the key is understanding why a project is dropping tokens and what actions it wants to encourage. Because demand for quality drops is high, clarity matters: read criteria, watch dates, and track updates. When you see a transparent purpose, a clean distribution plan, and active development, you’re looking at a healthier opportunity rather than a short-lived promotion.
Incentives: The Engine Behind Every Airdrop
Projects airdrop to bootstrap use: they want wallets, transactions, feedback, and social proof. In exchange, they share a small portion of supply so activity isn’t just bots or mercenary users. Your job is to align with the goal—use the app as intended, give high-quality feedback, participate in governance when invited, and document issues clearly. Teams recognize genuine engagement over time, so a consistent pattern of thoughtful interactions often scores better than random, superficial clicks that leave no value behind.
Common Airdrop Types and What They Reward
Most airdrops fall into three buckets: usage-based (on-chain actions, liquidity provision, volume), reputation-based (OG contributors, verified testers, community helpers), and referral or social (invites, content, educational quests). Usage-based drops usually require interacting with contracts on target networks. Reputation-based rewards value time in community channels, bug reports, or translations. Social drops can be easy but are worth less unless paired with real product use. Knowing the type helps you plan tasks efficiently and avoid wasting gas or time on actions that won’t count.
Defining “Profitable” Without the Hype
“Profitable” means the expected value of participation exceeds your costs: gas, time, tooling, and risk. Because outcomes are uncertain, think in portfolios of candidates rather than single shots. Track hours spent, fees paid, and the probability of allocation. Favor programs with public documentation, active builders, and clear, on-chain metrics. Then, when distributions happen, you can judge if your process is working and refine it, instead of chasing rumors with no data or post-hoc rationalizations.
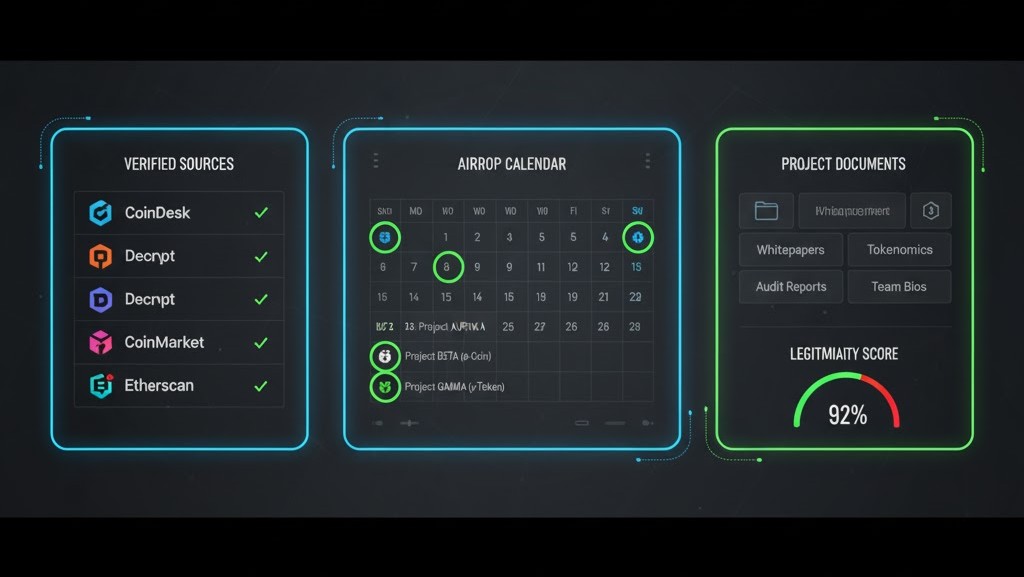
How to Find Quality Airdrops—Sources, Signals, and Proof
Finding strong candidates starts with reliable sources. Begin with official project channels, docs, and GitHub activity to see if shipping is real—not just marketing. Next, layer in reputable calendars, community dashboards, and on-chain explorers that surface testing quests, points, and eligibility hints. As you evaluate, look for consistent shipping cadence, transparent roadmaps, security disclosures, and credible backers. Finally, verify that your region is eligible and that any KYC is reasonable for the reward. This “source → signal → proof” pipeline prevents noise from eating your time and budget.
Official Pages, Docs, and Explorers
Always start at the source: project websites, documentation, and dev repositories. Docs explain goals, testnet steps, and snapshots; explorers confirm on-chain contracts and usage. Combine both to cross-check claims you see on social media. If a guide cites a contract address, look it up yourself; if a dashboard claims points, confirm the rules in docs. By looping source material into your workflow, you reduce rumor reliance and avoid being the last person to discover critical changes to eligibility or timelines.
Community Intel Without the Echo Chamber
Communities on Discord, Telegram, and X can surface early signals, but they also amplify noise. Follow contributors who post receipts—links to PRs, addresses, or commits—not just opinions. Bookmark a short list of curators known for accuracy and avoid overloaded channels that repeat the same screenshot. When in doubt, ask for sources. You will notice that the best scouts cite docs and on-chain proof. Over time, you will learn which voices consistently add value and which mainly chase engagement.
Reading Eligibility Clues Like a Pro
Most programs leave breadcrumbs: quests, allowlist hints, point systems, or “unique human” checks. Read the fine print: minimum actions, volume or time thresholds, or contributions like bug reports and translations. Take notes on cut-off dates and possible multipliers (e.g., testers on earlier versions). Also, note regional restrictions and KYC requirements—some drops exclude certain jurisdictions outright. By structuring this intel in a tracker, you act intentionally rather than guessing and hoping.

Getting Eligible—Wallet Setup, On-Chain Activity, and Costs
Eligibility usually means using the product the way the team wants. That begins with clean wallet setup, network funding, and enough gas to complete tasks. Keep a main wallet separate from a “quest wallet” to protect long-term holdings. Then, plan on-chain actions aligned with the airdrop’s type—swaps, liquidity, staking, bridging, or governance. Finally, control costs: use low-fee windows, batch tasks, and prefer L2s or high-throughput chains when possible. Good preparation turns stressful claim days into routine checklists.
Wallet Hygiene and Separation of Concerns
Segregate wallets: one for long-term assets, one for experiments and quests. Use unique email/handles only where required, and avoid reusing sensitive keys. Store seed phrases offline, enable hardware signing for higher-value activity, and revoke outdated approvals regularly. This structure limits blast radius if a test app fails and keeps your core portfolio safe. It also makes record-keeping easier when you later review which addresses qualified and how costs compared to outcomes.
The On-Chain Behaviors Projects Actually Reward
Projects reward sustained, meaningful use: executing core actions, providing liquidity where it matters, voting in governance, testing new releases, or reporting issues. Focus on the “happy path” the team is trying to validate. If the product is a DEX, do real swaps across a few sessions; if it’s a bridge, complete documented routes; if it’s a wallet, test features and report bugs. This authentic activity pattern distinguishes real users from sybils and aligns with how allocation formulas are increasingly designed.
Managing Gas, Fees, and Tooling
Track gas and fees before you start—don’t discover costs mid-quest. Use fee estimators and choose chains or L2s that match your budget. Consider batching transactions and avoiding peak hours. Tools like portfolio trackers, approval revokers, and CSV exports make reconciliation painless. If a task looks too expensive for a likely reward, skip it. Your edge is selectivity and discipline, not brute force.

Verification and Risk Control—Scams, Phishing, and Sybil Rules
Because airdrops attract attackers, risk control is non-negotiable. Validate contracts, double-check URLs, and watch for fake sites or Discord DMs. Never sign blind—read prompts, simulate transactions where possible, and revoke unnecessary approvals. Respect program rules too: many teams penalize multi-account sybil behavior, jurisdiction spoofing, or scripted abuse. In short, aim to be the user a project wants to reward: careful, honest, and constructive. That posture protects your funds and improves your chances of being recognized as a genuine participant.
Quick Legitimacy Checklist You Can Reuse
Before interacting, confirm the official domain, docs, and contract addresses. Look for security disclosures, audits, or at least threat models. Verify the team’s public activity and shipping cadence. If a claim page requests unexpected permissions or private keys, back out immediately. When something feels off, pause and ask for source links in public channels. A two-minute check can save you months of cleanup.
Phishing Defense and OPSEC Basics
Phishing exploits urgency: fake claim links, urgent DMs, or cloned interfaces. Use bookmarks for official pages, enable hardware confirmation for sensitive actions, and never import seeds into a website. Turn on two-factor authentication for related services and keep a clean browser profile for crypto tasks. After claims, revoke stale approvals and rotate exposed keys if you suspect any compromise. Small habits compound into strong protection.
Sybil, Residency, and Eligibility Pitfalls
Many programs now flag sybil patterns (clusters of similar wallets, mirrored timings, identical flows). If you manage multiple addresses for organization, keep behavior organic and avoid automation that mimics bots. Respect residency rules; using prohibited regions or falsifying KYC can forfeit rewards. When criteria are unclear, prioritize authenticity: test features, share feedback, and document legitimate participation with screenshots or tx links.

From Snapshot to Claim—A Step-by-Step Playbook
Airdrops revolve around snapshots—points in time when eligibility is measured. Your work is to prepare beforehand, then execute cleanly when the claim opens. Save the official announcement, note deadlines, and keep gas ready. On claim day, use the official page, confirm the contract, and sign the minimal approvals. After claiming, check vesting, transfer restrictions, and tax notes. This simple, repeatable workflow reduces errors and helps you move calmly even when timelines shift.
Before the Snapshot—Set Up and Document
Finish required actions early, and screenshot key steps. Add transaction links to your tracker and note which wallet performed which actions. If points or quests apply, confirm your totals before the window closes. This documentation helps resolve disputes and reminds you exactly what you did when allocations later appear. It also keeps you from repeating tasks you already completed.
On Claim Day—Verify, Sign, and Confirm
Only use the official claim URL. Check that the page matches the project’s domain and that your wallet displays the expected contract interactions. Sign the minimal approvals, wait for confirmations, and record the transaction hash. If gas spikes, pause—claims often remain open for days. Avoid multitasking or opening random links while signing; attention is your best defense against mistakes.
After the Claim—Vesting, Transfers, and Next Steps
Some allocations vest over time or restrict transfers. Read the fine print before moving tokens. If the asset lists on exchanges, spreads can be wide initially; avoid rushed decisions. Consider keeping a small portion to stay aligned with the project, especially if governance or future rounds depend on holding. Update your tracker with the amounts received, timelines, and any lessons learned.

Maximizing Rewards Efficiently—Time, Tracking, and Signals
The biggest edge is efficiency: spend your limited time on the highest-quality candidates. Use a simple tracker for tasks, costs, and probabilities. Batch low-fee tasks on the same chain and calendar recurring checkpoints (weekly scans for new quests, monthly reviews of outcomes). Over time, you’ll see which sources are accurate, which actions matter most, and which programs consistently deliver. By treating airdrops like a small research portfolio, you avoid burnout and improve your expected value.
Build a Lightweight Tracker That Actually Gets Used
Create columns for project, chain, actions required, deadlines, region/KYC, cost estimate, and status. Add links to docs, claim pages, and your transaction hashes. Keep it simple enough to update in two minutes. The point is not perfection; it’s making better decisions next week because last week’s data is visible and organized.
Time ROI—Batching, Windows, and Stop Rules
Group similar tasks by chain or wallet to minimize context switching and gas. Work in predefined windows (e.g., two sessions per week), and set stop rules when fees jump or rules change. If a program becomes unclear or abusive, exit quickly. This mindset turns a volatile queue of tasks into a calm, repeatable routine that fits your schedule.
Alerts, Automation, and Noise Filters
Use calendar reminders for snapshots and claim opens. Follow a short, curated list of researchers and official feeds with notifications on. Mute channels that spam unverified tips. Small automations—RSS for dev updates, saved searches for contract changes—catch real signals while keeping you out of the rumor treadmill.

Taxes, Compliance, and Security—Boring but Essential
Airdrops can be taxable events in many jurisdictions. While this guide is educational and not tax advice, it’s wise to record dates, fair value at receipt, and fees. Pair that with strong security hygiene: hardware signing for high-value claims, approval reviews, and cautious key management. Lastly, remember privacy: some reward programs ask for identity verification; decide in advance where you’re comfortable and keep that standard consistent. Sensible guardrails protect gains you worked hard to earn.
Simple Record-Keeping That Saves Time Later
Log the token, amount, date, approximate value, and transaction hash. Tag network fees and any subsequent sales or swaps. Export CSVs from your wallet or portfolio tool monthly. Organized records make tax season simpler and also help you analyze which activities paid off—and which weren’t worth the effort.
Security During Claims—Least Privilege Wins
Grant the smallest possible approvals and revoke them when finished. Prefer hardware confirmation for sensitive actions. Avoid connecting your main long-term wallet to experimental sites; use a dedicated claim wallet instead. If a claim requires unusual permissions, stop and ask publicly for clarification before proceeding.
Privacy Trade-Offs and Regional Rules
Some drops require KYC or exclude certain regions. Decide whether the reward justifies sharing data, and never falsify residency. Read privacy policies and check how long data is retained. When in doubt, skip programs that demand more information than you’re willing to provide; there will always be other opportunities.

Building a Long-Term Edge—Reputation, Diversity, and Learning Loops
Airdrops reward patterns over time. Build a reputation as a careful tester: file helpful bug reports, give respectful feedback, and vote thoughtfully when governance opens. Diversify across categories—DeFi, infra, gaming, identity—so you’re not tied to a single narrative. After each wave, run a short post-mortem: where did you earn, where did you waste time, and what will you change? This habit compounds and turns an uncertain pipeline into a structured, repeatable practice that fits your goals.
Become the User Projects Want to Reward
Teams remember wallets that provide signal: reproducible bug reports, clear screenshots, and constructive suggestions. When you show up consistently, you stand out from noise. Over several cycles, that credibility can influence allowlists, bonus multipliers, or community roles—benefits that rarely show up if your footprint is just one-off transactions.
Diversify Categories and Chains Intentionally
Split your efforts: a little infra testing here, a DeFi protocol there, perhaps a gaming or identity project when time allows. Rotate networks to manage fees and broaden experience. This approach reduces correlation risk and exposes you to new reward formulas that might favor the exact skills you’ve been practicing.
Post-Mortems That Actually Improve Results
After claims, review outcomes against your tracker. Which sources predicted accurately? Which actions were expensive but useless? Remove weak sources from your feed, double down on productive patterns, and update your templates. The goal isn’t perfection—it’s steady progress and fewer avoidable mistakes each month.









